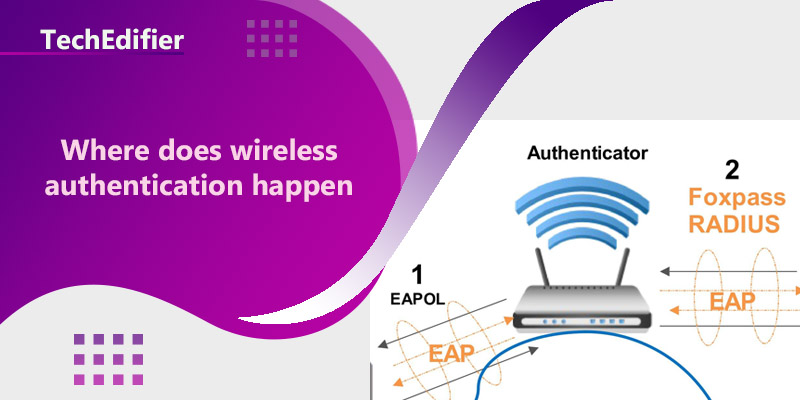
Wireless authentication happens when a device attempts to connect to a wireless network. The process typically involves the device sending a request to the wireless access point (AP) or wireless router to join the network. The AP or router then checks the device’s credentials, such as a username and password, to verify that the device is authorized to join the network.
There are several different types of wireless authentication methods that can be used, including:
- Open System Authentication: This method does not require any credentials and allows any device to connect to the network.
- Shared Key Authentication: This method requires the device to provide a pre-shared key or password to connect to the network.
- WPA (Wi-Fi Protected Access) and WPA2 Authentication: These methods use a combination of a pre-shared key and a four-way handshake to authenticate the device and establish a secure connection.
- EAP (Extensible Authentication Protocol) Authentication: This method uses a variety of authentication methods, such as certificates or tokens, to authenticate the device.
Once the device is authenticated, it is then assigned an IP address and can start communicating with other devices on the network.
How authentication is possible in wireless LAN?
Authentication in wireless LAN (Local Area Network) is possible through the use of a variety of methods, including:
- Open System Authentication: This is the simplest form of authentication, where no credentials are required. Any device can connect to the network as long as it is within range of the wireless access point (AP).
- Shared Key Authentication: This method uses a pre-shared key or password to authenticate devices trying to connect to the network. The device must provide the correct key or password in order to gain access to the network.
- WPA (Wi-Fi Protected Access) and WPA2 Authentication: These methods use a combination of a pre-shared key and a four-way handshake to authenticate devices and establish a secure connection. The four-way handshake process uses a combination of a client’s device MAC address and a pre-shared key to establish a unique session key.
- EAP (Extensible Authentication Protocol) Authentication: This method uses a variety of authentication methods, such as certificates or tokens, to authenticate devices. It can use different types of EAP such as EAP-TLS, EAP-TTLS, EAP-PEAP, EAP-FAST.
- 802.1X Authentication: This method uses a protocol called 802.1X to authenticate devices. It is typically used in enterprise networks and requires the use of a RADIUS server to manage authentication.
In summary, the authentication process in wireless LAN involves the wireless device sending a request to the wireless access point to join the network, the wireless access point checking the device’s credentials (username, password, certificate, etc.) to verify that the device is authorized to join the network, and once the device is authenticated, it is then assigned an IP address and can start communicating with other devices on the network.
People Are Also Reading:
👉 Top Reviews
- [Top Rated] Best Wifi Extender For Cox – Review In 2023
- [Top Rated] Best Bluetooth Speaker For Golf Cart – Review In 2023
- [Top-Rated] Best Bluetooth Ski Helmet Speakers
- [Top-Rated] Best Motorcycle Earbuds Noise Cancelling Bluetooth
- [Top-Rated] Best Bluetooth Headset For Truckers
👉 Top Tech News
- Can a laptop have its own internet
- How Many Bluetooth Headphones At Once
- Why laptop can’t connect to network
- Can Mobile Networks See Browsing History
- When wireless communication invented
👉 Top WiFi Routers
- Best Ubiquiti Router (gigabit internet)
- D-Link USB WiFi Adapter Dual Band AC1300 Top Features
- Why Does Xfinity WiFi Keep Dropping? 8 Solutions
- [Top-Rated] Best Modem Router Combo For Gaming – Reviews In 2023
- Can I use my modem with AT&T Fiber?